I. Intro
Purchase information: Separate payment is required for this feature. For more information, contact Support or your Customer Success Manager.
Lark now offers organizations the Bring Your Own Key (BYOK) solution to alleviate concerns related to storing data on public networks when using Lark. Organizations provide, use, and manage their own encryption keys for even greater data security.
Lark BYOK transfers the management of the encryption master keys to the organization. The organization can upload the customer master key (CMK) in an encrypted form to Lark and then securely decrypt it in the isolated key management service (KMS) for use. The CMK can be used to encrypt and decrypt all cloud data stored online by the organization.
In Lark, member data is encrypted with the data key and the data key is encrypted with the CMK. The data ciphertext and data key ciphertext are then stored in the member's database.
II. Structure
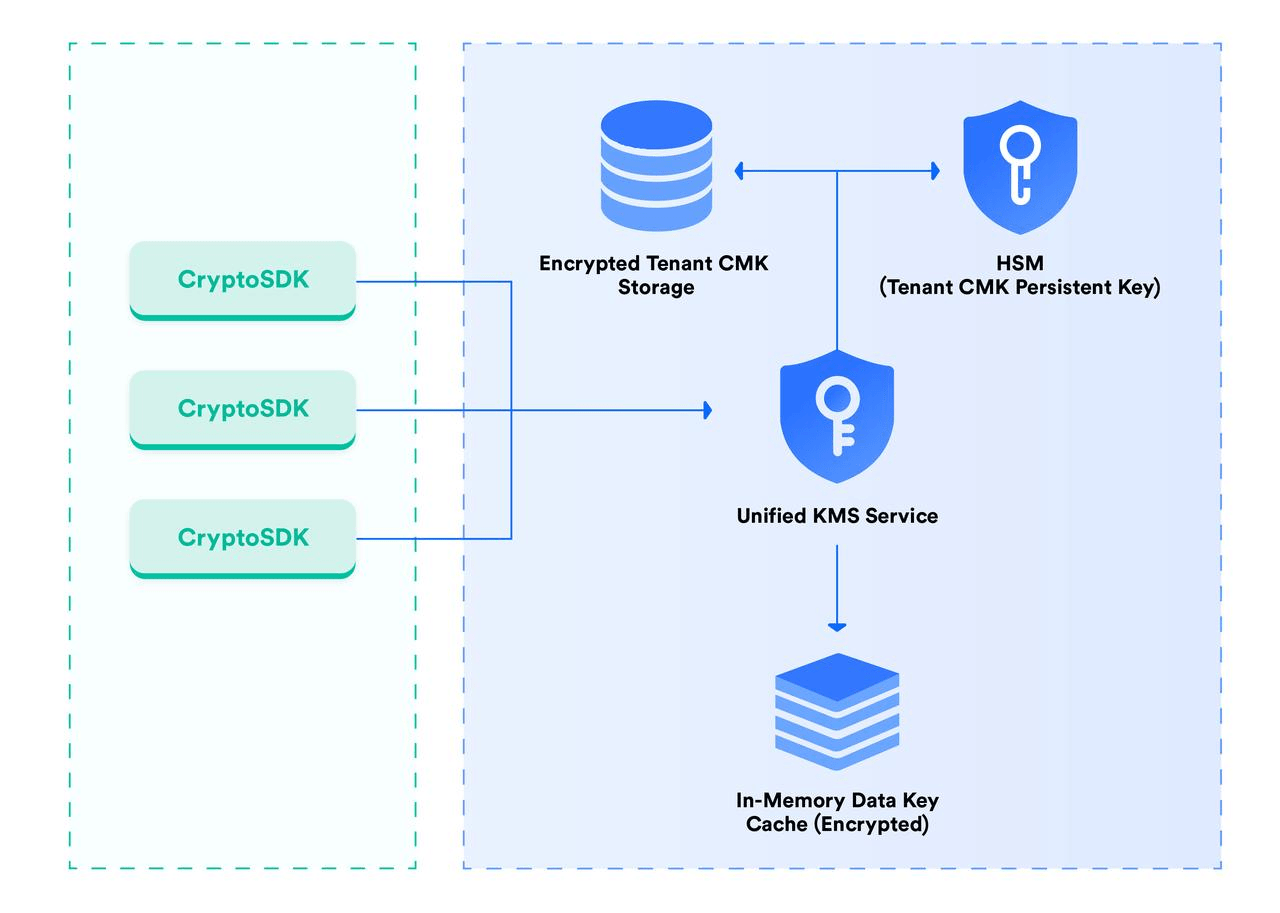
250px|700px|reset

- Both encrypted and decrypted business data is accessed through the CryptoSDK.
- The CryptoSDK communicates with the Unified KMS to acquire and rotate the data keys. This ensures the data key plaintext cannot be obtained.
- The Unified KMS generates an independent organization CMK Persistent Key for every organization. Once encrypted, the organization CMK Persistent Key is encrypted and stored in the Encrypted Tenant CMK Storage. The CMK Storage solution is a hardware security module (HSM). The CMK Persistent Key will be stored within the HSM and will not be removed. It can only be decrypted through the API. Auditing has confirmed the key is unable to be printed or output from the HSM.
III. Comparison with Lark SaaS
IV. Capabilities
- Organizations can import their own CMK into the Unified KMS.
- Changing keys: You can change the currently used keys and use new keys for data encryption.
- View keys: You can view all your organization's keys on the Unified KMS.
- Delete key: If a specified key is deleted, the data that was encrypted with it will no longer be accessible (this includes IM chats, online documents, video meetings, and calendar events).
- Restore keys: Re-import deleted keys to access data that was encrypted with that key (this includes IM chats, online documents, video meetings, and calendar events).
- Logs: View all actions undertaken with keys, such as action, action time, and assignee.
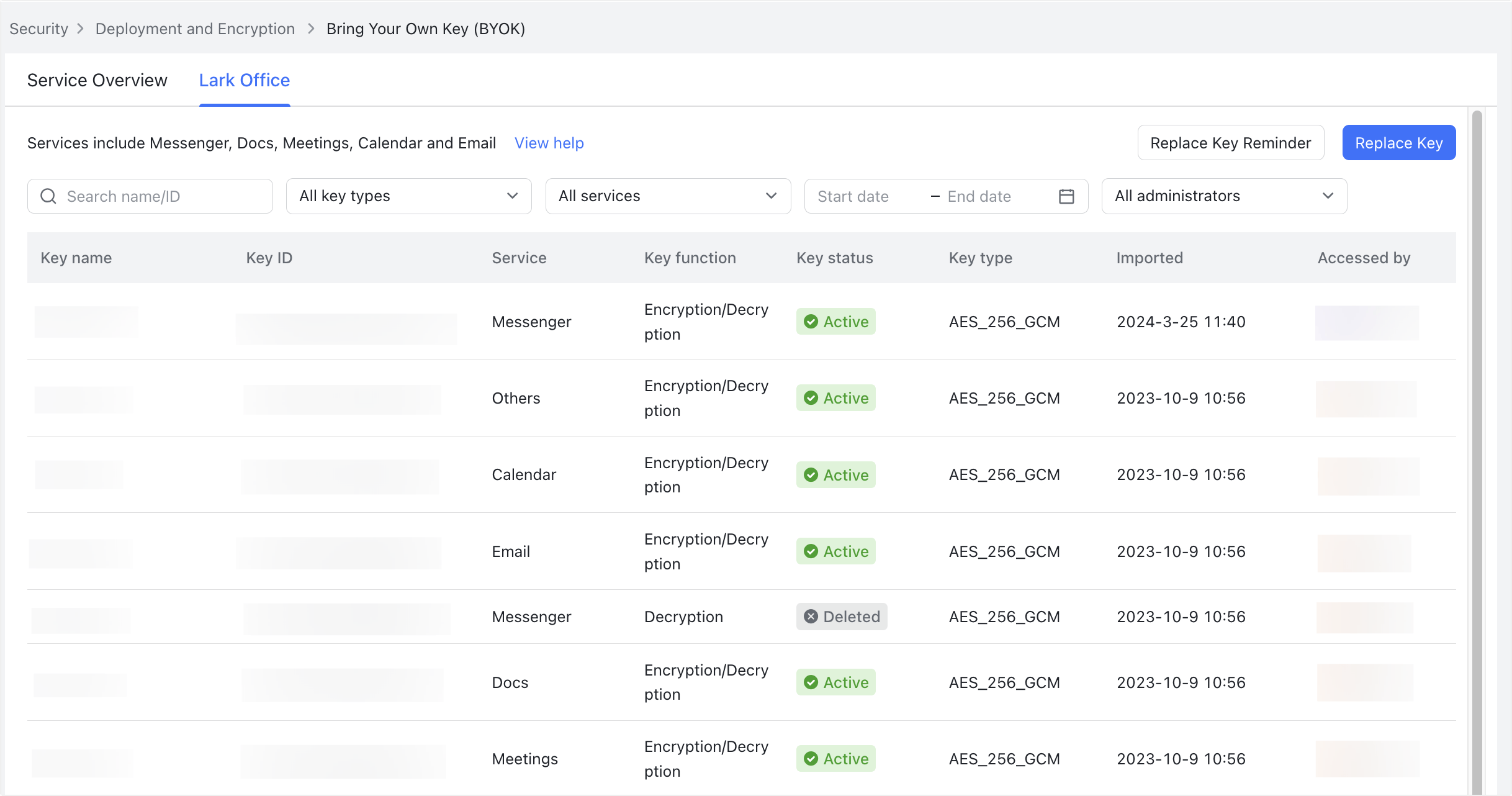
250px|700px|reset

V. Compatibility with Lark SaaS
- Switching from default keys to BYOK: If your organization used a system generated key to encrypt data, you can still replace this with BYOK. The newly imported key will be used for encrypting and decrypting data from here on. The previous default key will no longer be shown in the key list, but it will still be used for decrypting historical data.
- Switching from BYOK to default keys: You will automatically create a default master key for encrypting and decrypting new data. The previous BYOK keys imported by members will not be deleted, which can still be used for decrypting old data.
VI. Impact of using BYOK
- Structural view: After BYOK keys are imported, all organization cloud data will be encrypted and decrypted through the self-provided CMK. Organizations can import and rotate keys, manage the key lifecycle, and formulate their own key rotation policies. Lark default keys are used for encryption when BYOK keys are not imported.
- Member view: BYOK keys encrypt and decrypt data that is stored on a disk. This is an underlying technology which keeps stored data safe. This will not affect general users' experience when using Lark.
